Shreddy2 – The Raspberry Pi storage scrub station for USB thumb drives
"Delete early, delete often" is the slightly adapted slogan reminding to minimize data leakage via lost or stolen USB thumb drives by frequently cleaning them. Are you tired of being focused to not accidentally erase the wrong USB device on your local computer when formatting an USB stick? To simplify the process, we implemented an USB eraser station software, which runs on a Raspberry Pi and that cleans USB sticks. Therefore, shreddy, ready, go!
Disclaimer
First of all, sensitive information should not be stored on mobile USB sticks without any protection, especially when there is the risk of losing it. It is always a good idea to encrypt data before storing it or to use an USB stick that supports encryption that you trust, or even better, that has been verified. Nevertheless, a lot of data is still stored on USB sticks and if it is not deleted regularly, there will be a pile of information that even if single files are less sensitive, the large quantity of files could reveal a lot about internal activities or personal matters. Therefore, deleting files on a USB stick from regularly mitigates the impact in the event of loss.
Deleting data on Flash
USB sticks are built from Flash memory and deleting files does not really remove the data. File contents could be recovered on the file system layer, especially on FAT file systems that are widely used on USB sticks, as long as file contents are not overwritten. But even then, corrupt file residues could still contain enough extractable information. Back in the days, files on magnetic discs were overwritten with secure deletion tools that wrote data multiple times over files to make recoverability unlikely. While this works for magnetic discs, this does not work with Flash storage. The Flash memory controller tries to spread write operations over Flash memory to ensure an equal utilisation of memory cells. This method is called wear levelling and extends a storage media’s lifespan. This wear levelling makes it impossible to just overwrite a single file to remove its content, because several regions within the Flash memory may have been overwritten, but not the location where the original file content was stored. Furthermore, the Flash memory controller reserves extra storage that is used when memory cells degrade too much and fail. If file content was written to such a now inaccessible location, it cannot be overwritten anymore without low-level access to the Flash memory.
So, what is the correct way to clean an USB memory stick? NIST SP 800-88 Rev. 1 “Guidelines for Media Sanitization” recommends the following procedure for erasing USB Removable Media (including so-called Pen Drives, Thumb Drives, Flash Memory Drives, Memory Sticks, etc.):
Overwrite media by using organizationally approved and tested overwriting technologies/methods/tools. The Clear pattern should be at least two passes, to include a pattern in the first pass and its complement in the second pass. Additional passes may be used.
But NIST also adds as a note: “For most cases where Purging is desired, USB removable media should be Destroyed.” That is the recommendation to be on the safe side.
However, for less critical data and piles of data a simple overwrite approach with multiple passes may be sufficient. Since single file overwriting does not work due to how Flash memory is managed, a full overwrite approach reduces the risk of residues significantly. Wei et al observed in their practical recoverability tests:
In most cases, overwriting the entire disk twice was sufficient to sanitize the disk, regardless of the previous state of the drive. There were three exceptions: about 1% (1 GB) of the data remained on Drive A after twenty passes. We also tested a commercial implementation of the four-pass 5220.22-M standard on Drive C. For the sequential initialization case, it removed all the data, but with random initialization, a single fingerprint (remark: test data previously spread over the medium) remained.
In other words, there is no real correct way of secure data deletion other than encrypting the data and deleting the key or physically destroying the medium. Don't tell us you haven't been warned. Nevertheless, we created a tool if you would like to try to erase data.
Software
We implemented a software in python that uses the py-udev library to listen for
events caused by plugged in USB storage devices. Storage media are then
overwritten in three passes: The first and second pass use the badblocks
command to write the complementary
patterns 0x00 and 0xff. The badblocks command is not intended to be used for
wiping, but does this as a side effect when looking for bad blocks. The tool is
used here, because it allows specifying an explicite write pattern. Overwriting
the block device in a third pass is implemented via invoking the shred command in random mode. Overwriting the
memory with random data should increase the effort for searching for
extractable residues. Afterwards, the software creates a new FAT32 file system.
For this, the program relies on parted and mkfs.
The software can be installed on a Raspberry Pi that is placed in an office in a trustworthy environment. People can plug in their used USB sticks and come back later to pick it up, which might be a security problem on its own. Again, you have been warned.
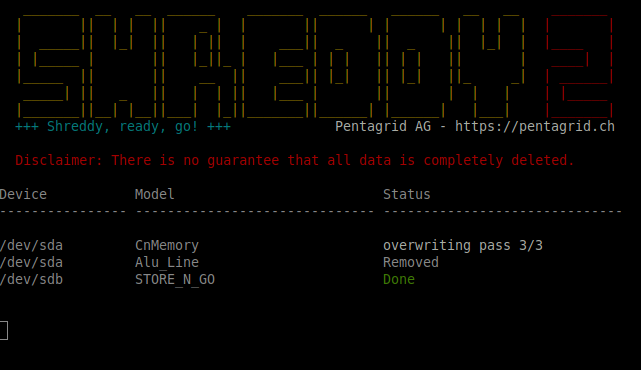
The software implements two methods to signal the status. In a networking mode,
the eraser station has network connectivity and you can request status
information via netcat or telnet (cf. screenshot above). Since the networking mode
allows a possibly compromised Raspberry Pi to extract the USB stick contents
and to exfiltrate data to an attacker, the Raspberry Pi could alternatively put
into a metal case to block radio interfaces and to furthermore operate it
without Ethernet. The second status signalling method is an USB busylight
attached to the Raspberry Pi. As long as there is an erase operation running,
the busylight shows red, a red flashing reports an error, and a green light
means all plugged-in USB sticks were processed. When idling and there is no USB
memory stick inserted, the busylight saves power and is off. The software
currently supports Kuando busylights via the pyBusylight Python library.
The source code is available on Github, where there is also the installation guide.