IBIS hotel check-in terminal keypad-code leakage
After a hacker congress in Hamburg, Pentagrid noticed that an IBIS Budget hotel check-in terminal leaked room keypad codes of almost half of the hotel rooms, when a users searches for a specific form of a non-alphanumeric booking number. Access to hotel rooms would allow the theft of valuables, especially if low-budget hotel rooms are not equipped with a room safe. The hotel chain operator Accor has fixed the problem in the meantime.
Timeline
2023-12-31: Vulnerability found at a check-in terminal in Hamburg.
2024-01-01: First oral report of the vulnerability to the franchisee Sczygiel Hotelmanagement GmbH.
2024-01-02: Initial draft of the advisory.
2024-01-02: Found security.txt information for ibis.accor.com, which references the Yagosha portal as contact for vulnerability reporting. This program requires written consent for publication, which is not compatible with Pentagrid's coordinated disclosure policy. An older version of the security.txt lists security@accor.com as contact, which is also the GPG contact identifier in the current security.txt.
2024-01-02: First written contact to security@accor.com.
2024-01-02: Reported status to franchisee.
2024-01-03: Response from security@accor.com and expression of the wish to not go public and to use the Yagosha program.
2024-01-03: Tried to clarify further handling of the coordinated disclosure and publication mode.
2024-01-11: Contacted Accor security team again after not getting any further response and sent vulnerability details. Set a deadline for an initial response to the finding by 2024-01-15.
2024-01-11: Received response from security team that they do not accept submissions via e-mail, but only via the Yogosha program and Pentagrid should refrain from sending further mails via the e-mail channel.
2024-01-11: Pentagrid reponded that the consequence of not responding until deadline is a publication of the vulnerability, in this specific case without details that would allow an exploitation, at least not for the moment.
2024-01-16: Deadline for publication after 14 days for no reaction according to Pentagrid's coordinated disclosure policy. However, Pentagrid deferred an early publication.
2024-01-18: Pentagrid asked Accor Security for a status regarding problem verification and fixing timeline.
2024-01-25: Pentagrid repeated status request, because Accor did not respond.
2024-01-26: Accor confirmed that vulnerability can be reproduced, was fixed and deployed to affected check-in terminals.
2024-04-02: Deadline for publication after 90 days and publication of the advisory.
Keycode leakage
CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N, 5.3 Medium
Affected Components
Pentagrid identified the vulnerability for the check-in terminal with the ID 2711 in Hamburg Altona. The vendor and product of the terminal is unknown to Pentagrid. Other terminals are likely affected as well. According to a Google image search for these types of check-in machines, they are used for several IBIS Budget hotels in Germany and other European countries.
Summary
If the hotel reception is not staffed, guests can register via a check-in terminal. The terminal also supports the lookup of existing bookings. With a booking ID, guests can lookup their room number and keypad code. However, when entering a '------' as booking ID, the check-in terminal lists other people's bookings and keypad codes.
Impact
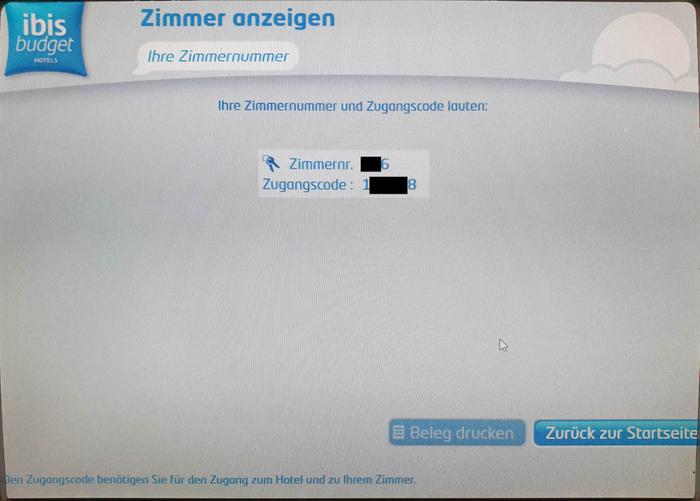
The check-in terminal leaks sensitive information containing the room number and the keypad code. The keypad code is does not change during the stay. Therefore, the keypad code information allows physical access to hotel rooms.
Technical Details
To use the check-in terminal's lookup function for existing hotel bookings, a guest needs to enter the booking ID. As far as observed, it is an eight-letter code. With a given booking ID, a guest can look up the room number and the room's keypad code. The keypad-code is a six-digit numeric code.
For an invalid booking ID, the terminal displays a message indicating the booking ID is not known. If a guest does not enter a booking ID but enters '------' instead, the check-in terminal lists bookings. Any other sequence of dashes is accepted if it is long enough to enable the submit button. Therefore, it is assumed that a variable length string is likely not a master code, but a bug or a not deactivated test function.
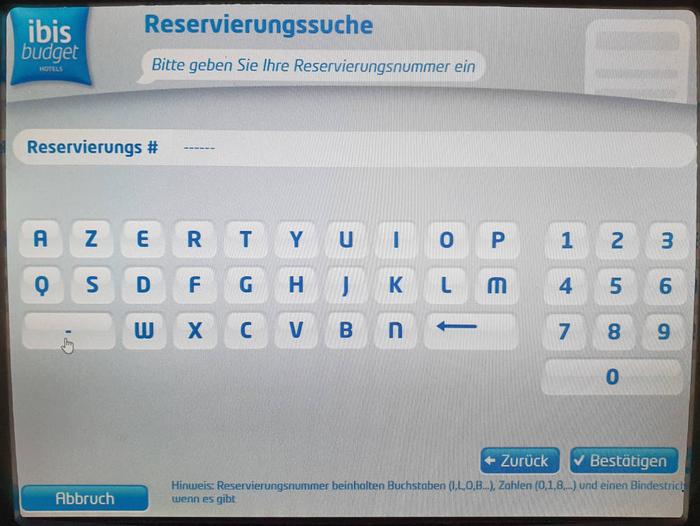
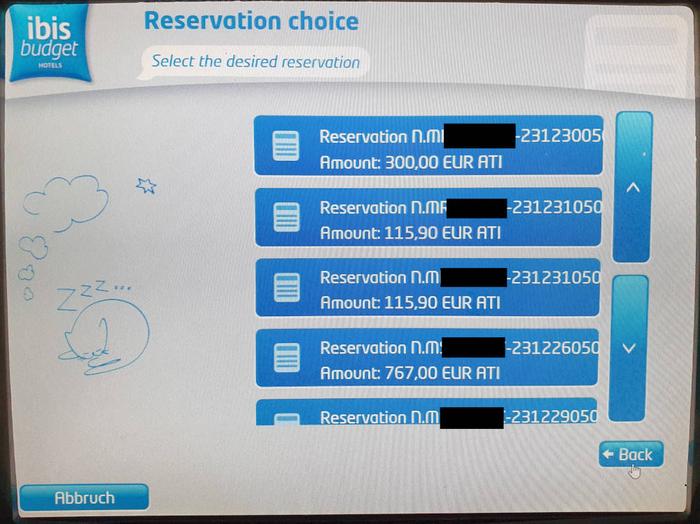
The list of bookings contains the booking ID, a timestamp (likely the expected arrival date) and the total price, which may give an indication how long a guest will stay.
Selecting a booking shows the room number and the keypad code, which would allow access to other guest's hotel rooms.
We published a demonstration video on Vimeo.
For the hotel, where this findings was found, the list contained 87 booking entries. According to reception staff, the hotel has 180 rooms.
Only requiring a booking ID to get the room code is straightforward for the guest, but potentially not secure. Booking IDs may leak through discarded invoices and print-outs.
Precondition
An attacker needs physical access to a check-in terminal. The terminal must be in a state where it allows self-service, for example during night times. Further preconditions are not known to Pentagrid, but could exist.
Recommendation
Recommendation for Accor/IBIS and the vendor:
The vulnerability should be addressed by requiring a valid booking ID for the lookup.
The terminal should ask for further data, usually not documented in booking confirmations or invoices. Otherwise a thrown away invoice or booking confirmation could lead to room access. This could be a PIN code, because people usually recognise a PIN code as a confidential information and would be less likely to disclose this information.
Affected hotels should be informed about the vulnerability in general as early as possible with recommendations for preliminary actions. Once a fix is available, the recommendations for actions should be updated and hotels informed about the change.
Bookings should be removed from the terminal as early as possible as a precaution, for example after printing out the room data or after looking up the booking.
Recommendation for franchise hotels:
The terminal should be disabled as long as the problem is not fixed.
Once, patches are available, the franchisee should install the software update and should verify that the problem is solved.
Credits
This vulnerability was accidentally found by Martin '------' Schobert (Pentagrid).