Burp Suite - solving E-mail and SMS TAN multi-factor authentication with Hackvertor custom tags
Why bother investing time to automate work when doing IT security testing? On one hand, manual testing is a tedious work, where you spend time doing vulnerability tests that could be done by a machine. On the other hand, letting a machine decide fully on its own on how to do tests will mostly result in the machine doing nothing useful. This is especially true for security testing, where manually checking every parameter for injection attacks is very laborious and automated security scanners go on scanning for hours while a human would have aborted the scan for various reasons. However, if we teach automated tools to do things correctly each time, we get the sweet middle spot of semi-automated security testing, where the tools do the automatic and systematic security tests and the analyst can focus on the parts of a security test, where the tools are likely insufficient.
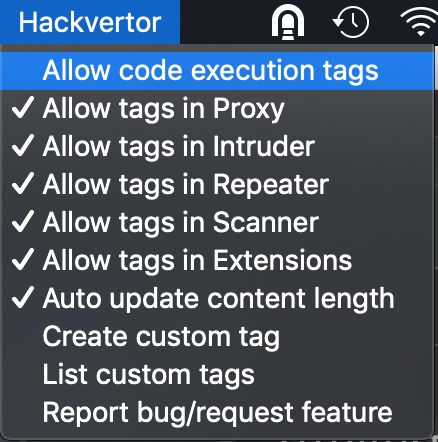
Burp Suite Pro is one of the main tools to do all kind of HTTP related security analysis and that supports a semi-automated testing. But now and then it lacks certain features. Burp extensions can again add some of them. In this post we would like to show how to use one of the most powerful extensions, Hackvertor by Gareth Hayes and its relatively new feature of Python scripting.
Use Hackvertor to fetch second-factor authentication token
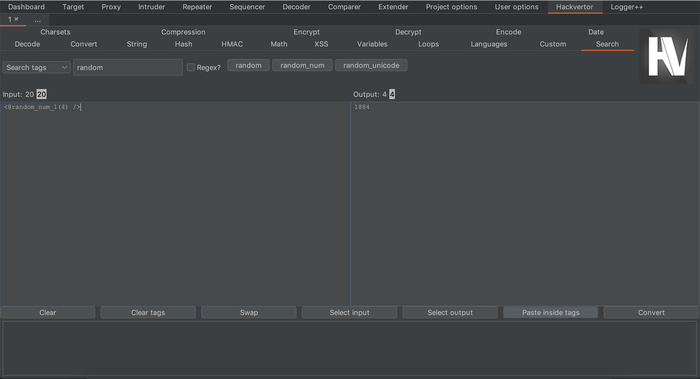
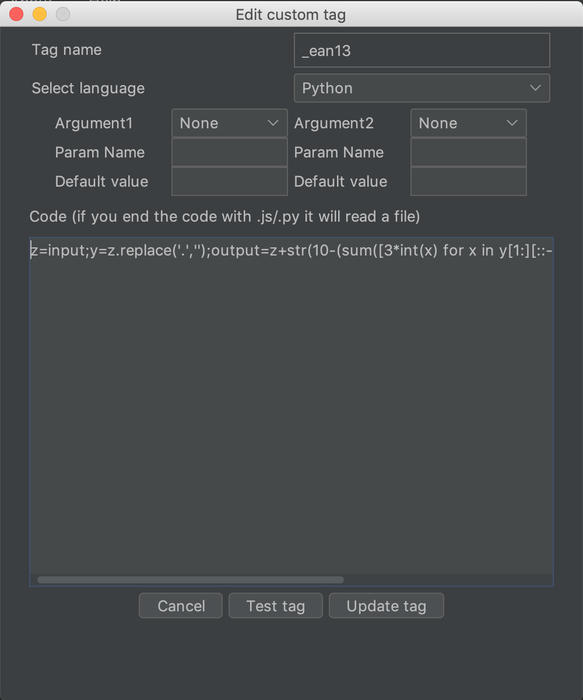
Let's do a more advanced custom tag example. Could you use the scripting capabilities of Hackvertor
to automatically solve TAN second factor verification in multi-factor authentication web forms? At
Pentagrid we have an SMS to E-mail gateway for pentesting purposes, meaning if second factor TANs are
sent out via SMS or E-mail, they will always land in one of our testing E-mail inboxes. Can we
retrieve the second factor TAN tokens from the E-mail inbox with a Hackvertor tag? Yes we can, with
the very useful Python imaplib and an E-mail server that supports IMAP. Of course the entire
parsing logic for the incoming TANs is highly dependent on the web application and how the SMS or
E-mails look like. You will need to change the parsing code according to your needs. So here's a
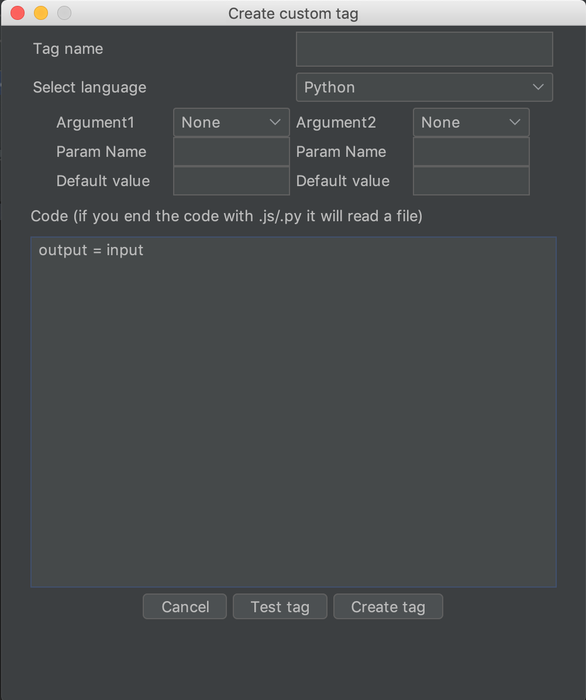
quick'n'dirty example that worked for us for a certain web application. We created the new Hackvertor
tag like this:
import getpass, imaplib import time time.sleep(0.1) class Email: def __init__(self, data): self.data = data.decode() self.body = "\r\n\r\n".join(self.data.split("\r\n\r\n")[1:]) M = imaplib.IMAP4_SSL(host='use-your-own-mail-host') # warning: no certificate verification M.login("pentagrid@example.org", "email-password") M.select() typ, data = M.search(None, 'ALL') token = "NO TOKEN WAS FOUND" for num in data[0].split()[::-1]: typ, data = M.fetch(num, '(RFC822)') email = Email(data[0][1]) for line in email.body.splitlines(): #print(line) if line.startswith("Your TAN is: "): token = line.split("Your TAN is: ")[1].strip() if token: print(token) break else: print("No token found") #print('Message %s\n%s\n' % (num, data[0][1])) print("Final token:", token) output = token M.close() M.logout()
The Python code will login to the IMAP mailbox, retrieve E-mails starting with the newest,
quick'n'dirty parse the TAN from the E-mail by interating through each line of the E-mail
and assign the the first token found to the output variable that Hackvertor expects.
You might need to play with the sleep delay we introduced at the beginning of the script
to make sure the E-mail reaches the mailbox before you try to retrieve it. Otherwise you
could change the script to only consider the very newest E-mail but you would need to take
care to delete old E-mails. And of course you need to change your E-mail server, username
and password. Please be aware that this is as well not thread-safe, you would need a
seperate E-mail mailbox for each thread to make it concurrent.
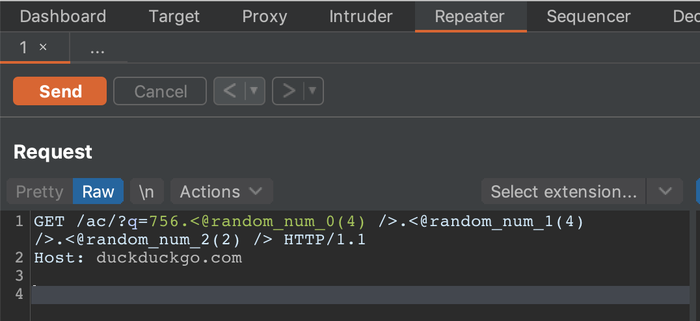
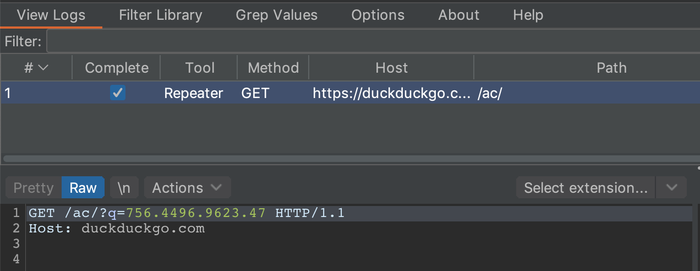
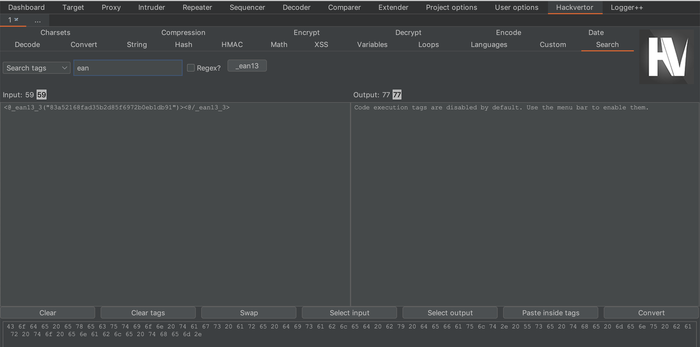
Configuring a search and replace rule in the Burp Proxy to replace any second factor you enter with the Hackvertor tab is left as an exercise to the reader. We were able to test websites without ever entering the second factor manually again, as the entered token was replaced with a Hackvertor tag and Hackvertor fetched the token from the mailbox.
Hackvertor is therefore the perfect solution if you would like to script things that are sent in HTTP requests. With the new scripting capabilities, it is not necessary to write extensions when you want to change things sent out. Or do you? Unfortunately, there are certain limitations with this approach and in Burp. The search and replace rule for the Proxy of course only works for the Burp Proxy. But what if we want to make the Burp Crawler be able to login with second-factor TANs? We can't use session handling rules (another advanced topic of Burp), as they don't apply for Burp Crawler. But we were able to write an extension that handles that part, but that's for another blog post (it is really cool to see the headed browser of Burp login correctly). And what if you would also like to modify HTTP responses? Or what if you would like to even enhance Burp with a Transfer-Encoding feature it does not yet support? Do you want to know how you could set up an SMS to E-mail gateway? Stay tuned for our next blog posts, subscribe to our RSS feed or follow us on Twitter or LinkedIn.
Update 2025-06-04: An update of Hackvertor in 2025 changed the style of closing elements from <@/name> to </@name>. Therefore, we updated the post, but not the screenshots.